User:Ajak/Security Notes
I do a bit of security bug wrangling for Gentoo. Here are some quirks with upstreams and other things related to that I think it would be useful to document. For most of the software mentioned here, release announcement mailing lists and other announcement methods can be found on Sam's release announcement page.
In general, I use my secbug-file script to file security bugs.
Software-specific information
Oracle CPU Advisories
Oracle provides quarterly critical patch updates for their software. The advisories for these announce vulnerabilities discovered in their software (example). Gentoo carries several of these softwares, including several of their forks which are generally vulnerable to the same vulnerabilities. They will need bugs filed if affected by any announced vulnerabilities:
Java
We don't have dev-java/oracle-{jre,jdk}-bin themselves in tree anymore (bug 732630, bug 717638), but we still have dev-java/icedtea{,-bin} and dev-java/openjdk{,-jre-bin,-bin}.
Virtualbox
No surprises here, app-emulation/virtualbox.
MySQL
Not only can there be vulnerabilities in dev-db/mysql itself, but also sometimes dev-db/mysql-connector-c{,++}, and the Java connector dev-java/jdbc-mysql.
It has a couple forks and their own associated softwares too: dev-db/percona-server, dev-db/mariadb{,-connector-c}. Not all of the issues affecting MySQL will affect MariaDB, so generally we should wait until MariaDB upstream makes their own advisory before making the MariaDB bug, as annoying as that may end up being with mangling trackers.
Chromium
Edge
Microsoft security advisories are a lot of spaghetti, just use: https://learn.microsoft.com/en-us/DeployEdge/microsoft-edge-relnotes-security
Mozilla
My mozsec.py script is useful for enumerating vulnerability IDs used in Mozilla advisories.
user $./mozsec.py 1 # Where 1 is the first set of advisories from first on https://www.mozilla.org/en-US/security/advisories/ Tracker CVEs: CVE-2022-40956, CVE-2022-3266, CVE-2022-40960, CVE-2022-40959, CVE-2022-40957, CVE-2022-40958, CVE-2022-40962 Firefox ESR 102.3, Firefox 105 CVE-2022-40961 Thunderbird 102.3 CVE-2022-3155
Misc
MITRE/ Redhat Scope
MITRE is typically the catchall assigner for CVEs. Almost always, if a piece of software is not covered by a CNA, CVEs for that software are assigned and updated by MITRE. Recently however, MITRE has apparently offloaded some of this responsibility onto RedHat for certain software. In practice, this means CVE update requests sent to MITRE for certain software will be met with a response to direct the request to secalert AT redhat.com, even if the CVE was originally assigned by MITRE. Affected software discovered so far are dev-db/postgresql and dev-lang/python.
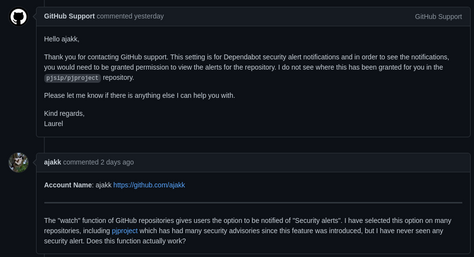
Github "security alerts" watch option
It seems clear to me based on the existence of this option that this would notify watchers of the repository of Github Security Advisories (GHSAs issued via the Github "security advisory" mechanism). According to Github support, this is actually not the case and the watch option only refers to Dependabot security alert notifications, which users have to be whitelisted to receive.