File:Firejail seccomp example.png
From Gentoo Wiki
Size of this preview: 800 × 320 pixels. Other resolutions: 320 × 128 pixels | 1,280 × 512 pixels.
Original file (1,280 × 512 pixels, file size: 88 KB, MIME type: image/png)
Summary
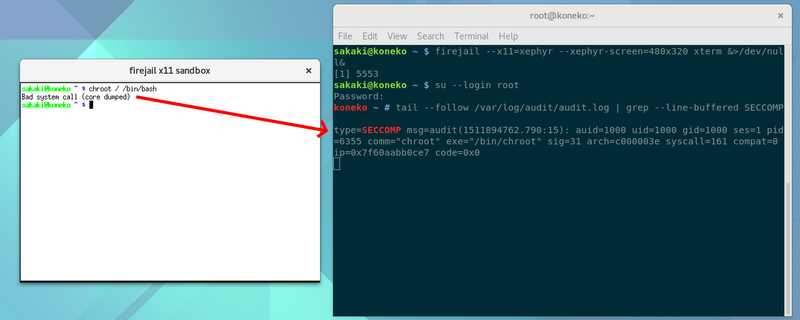
Screenshot of an xterm running in a xephyr window (started using firejail from the command line in parent desktop), in which "chroot / /bin/bash" is attempted, to illustrate firejail's seccomp-bpf syscall filter (shows message written to audit log, and that the chroot process itself dumps core, with a "Bad system call" message). Uploaded for use in a forthcoming mini-guide on X11 sandboxing (an addendum to Sakaki's EFI Install Guide).
Licensing
This asset is licensed under the terms of the Creative Commons Attribution-ShareAlike 4.0 International license.
You are free to share (copy, distribute and transmit the work) and remix (adapt the work), but you must attribute the author and distribute any derivative works you create under a similar license.
You are free to share (copy, distribute and transmit the work) and remix (adapt the work), but you must attribute the author and distribute any derivative works you create under a similar license.
File history
Click on a date/time to view the file as it appeared at that time.
| Date/Time | Thumbnail | Dimensions | User | Comment | |
|---|---|---|---|---|---|
| current | 19:03, 28 November 2017 | 1,280 × 512 (88 KB) | Sakaki (talk | contribs) | Screenshot of an xterm running in a xephyr window (started using firejail from the command line in parent desktop), in which "chroot / /bin/bash" is attempted, to illustrate firejail's seccomp-bpf syscall filter (shows message written to audit log, and... |
You cannot overwrite this file.
File usage
The following page uses this file:
